[SECURE] phemex.com cannot be exploited by leaked login credentials
Summary:The exchange platform phemex.com cannot be exploited by leaked login credentials, significantly reducing the risk of account takeover (ATO).
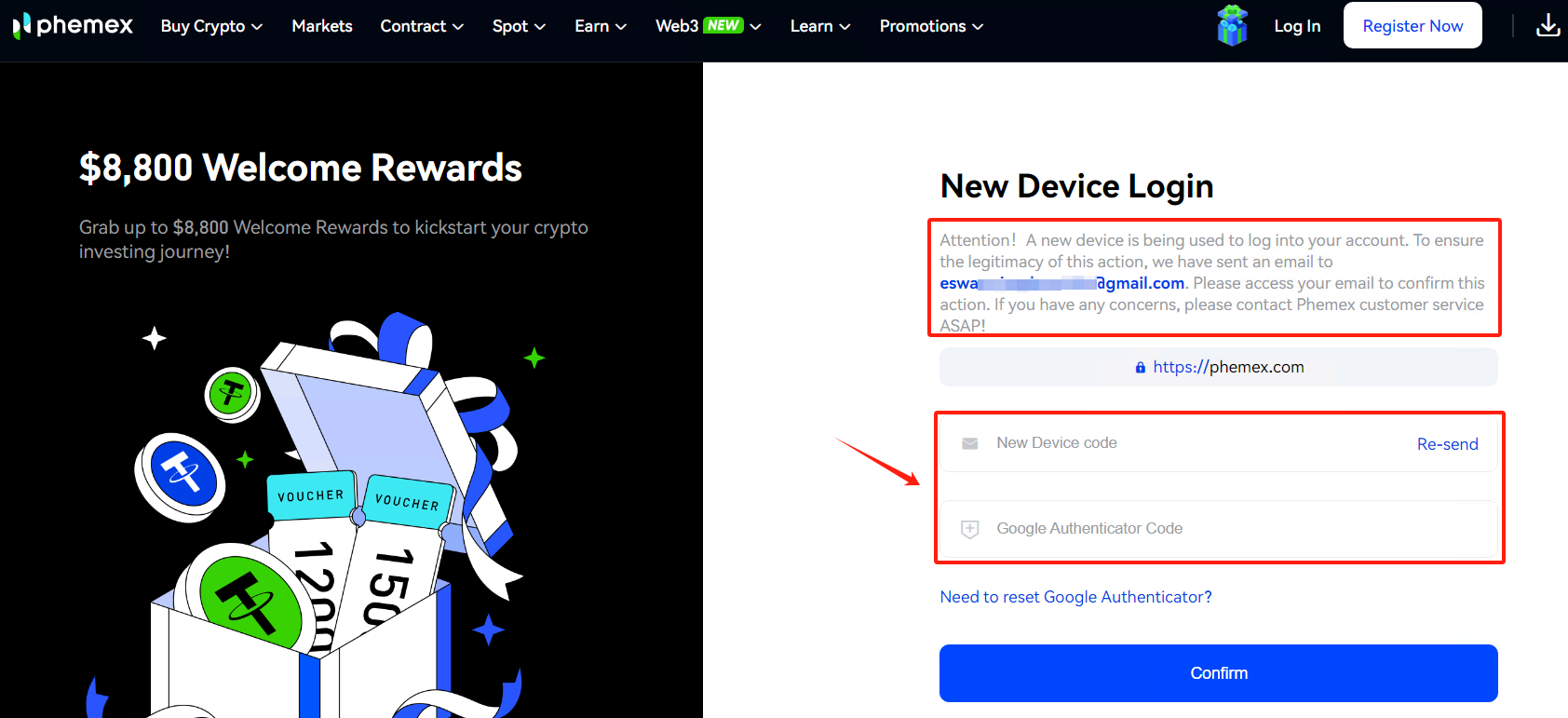
THUD TECHNOLOGY PTE. LTD. (darkweb.vc) conducted an exploitation test on the login credentials leak for the exchange platform phemex.com. When attackers attempt to log in, even if the login credentials are correct, the platform will trigger two-factor authentication methods such as Google Authenticator upon detecting abnormalities like device changes, ensuring the security of the account. Therefore, we have detected that even though there is a leak of login credentials for at least 40,000 accounts on phemex.com, attackers still face significant difficulties in leveraging these leaked credentials to conduct account takeover (ATO) attacks against phemex.com.
Despite this, We still recommend notifying the website's members of the leaked login credentials through 'Dark Web Reports', urging them to promptly update their credentials. Regardless of whether 2FA is implemented, securing leaked accounts by locking them and resetting login credentials is a robust security measure. Additionally, it’s advisable to alert affected users to change their passwords immediately. DarkWeb.vc offers highly cost-effective intelligence on login credential leaks to enterprises.